The other day this video by LowLevelLearning (recommended HERE) appeared on my YouTube homepage. Despite the clickbait title, it intrigued me, so I bought a CH341A to do some experimenting (here's the amazon link of the one I got).
Will this be the first post in a series? Maybe, IDK
Introduction
The vast majority of embedded devices uses one of these three types of flash memory to store the firmware that makes them work: NAND, eMMC or NOR flash.
NAND flash are described as "high capacity" memories, and are typically used in USB pendrives. In the embedded world they are present in devices that needs a more-than-basic firmware, like smart TVs or high end routers.
eMMC are used in high end devices like smartphones, tablets, computers, but it's not the target of what I'm doing today.
What we are going to use are NOR flash: these kind of chips are used for devices that requires low capacity storage, data operations are executed byte per byte, and SPI, Serial Peripheral Interface, is the protocol that they use to communicate with other components. These chips are usually contained in the SOIC8 package (8 pins).
The Target
The first device I used the CH341A on is a TP-LINK WA850RE 300Mbps Universal Wi-Fi Range Extender. It's probably the cheapest and most common wireless range extender you can find, and there's a small chance you have something like that laying around in a closet (like I did).

Anyway, I smashed it open to get to get access to the board, and after having performed a careful and in-depth analysis thanks to my incredible skills in electronics and stuff, I identified our target, the NOR flash memory IC (spoiler: the one that looked bigger and had 4 pins per side).
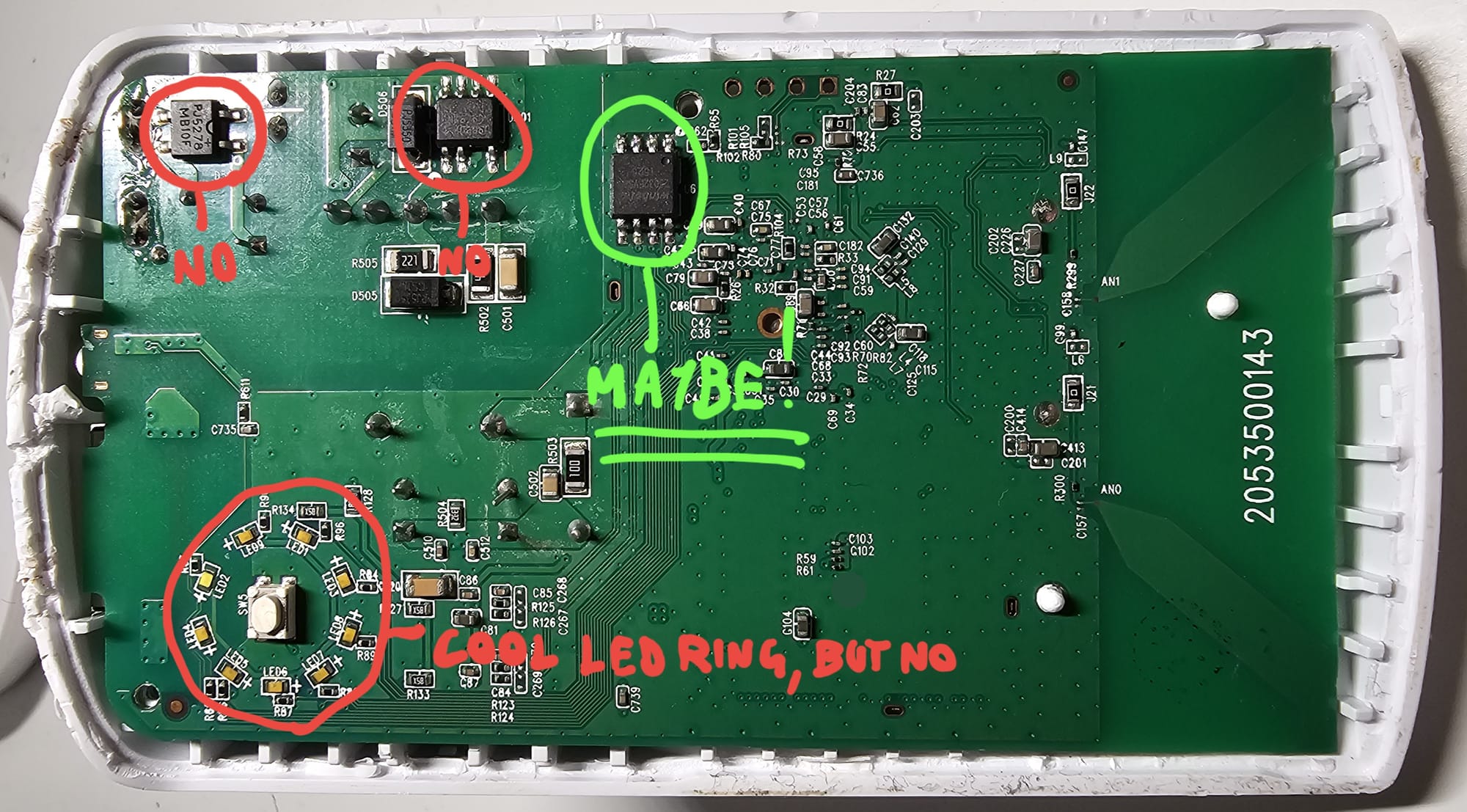
Before frying the board, I wanted to make sure that the one I chose was the right IC, so I checked the label on it

And yup, it seems to be the right one!!
Dump!
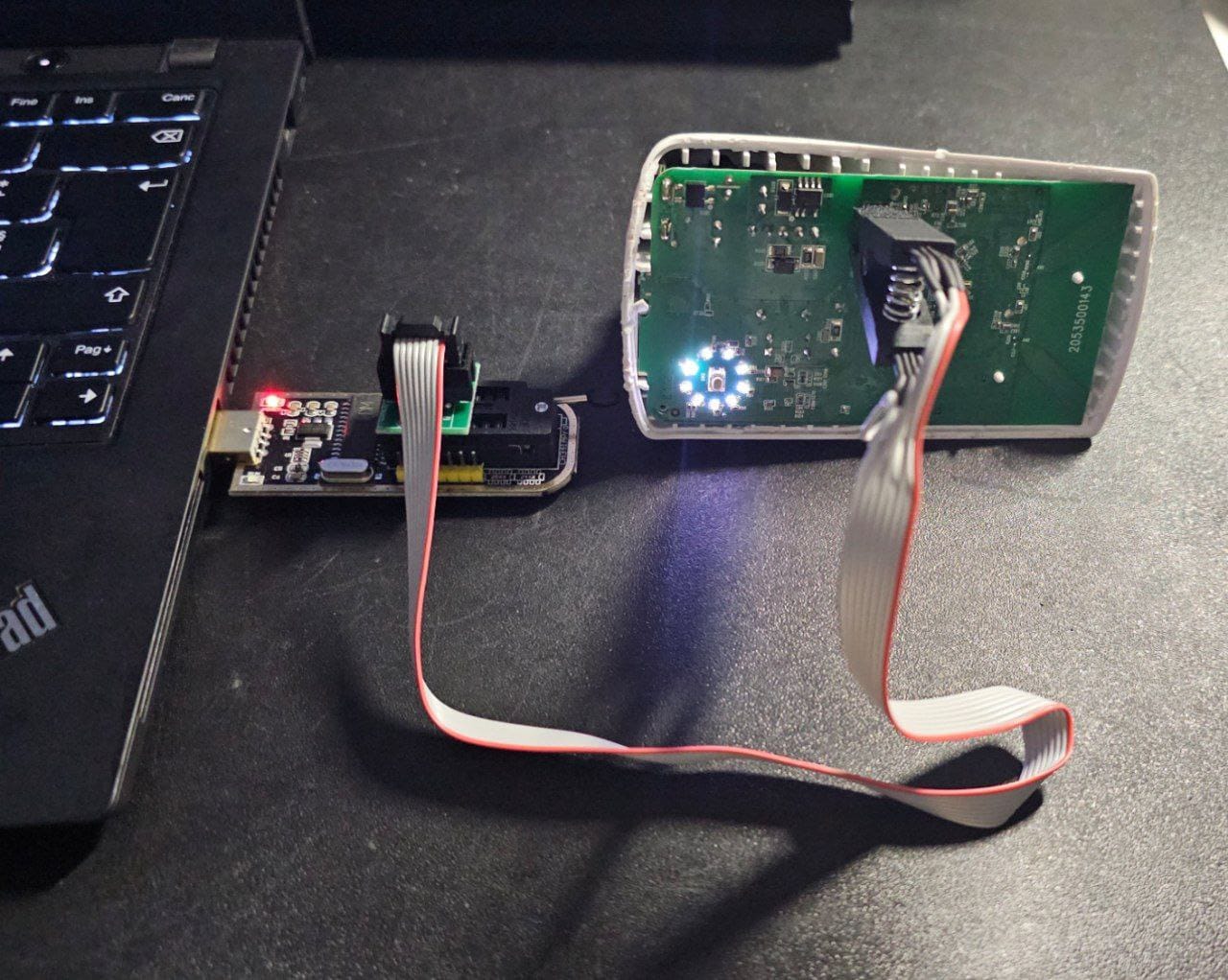
After the physical setup of the CH341A and the alligator clip to the repeater (remember, the red wire needs to align with the first pin on the chip), we can use flashrom to actually extract the firmware
The first try, of course, failed
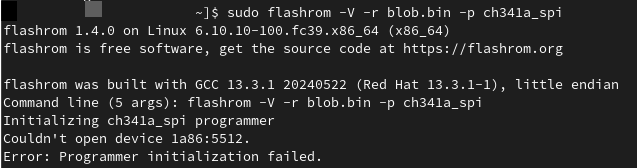
But after a bit of trial and error, I got this
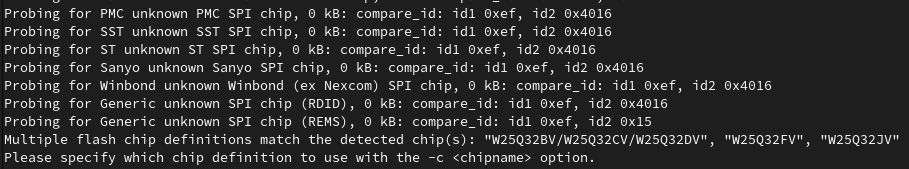
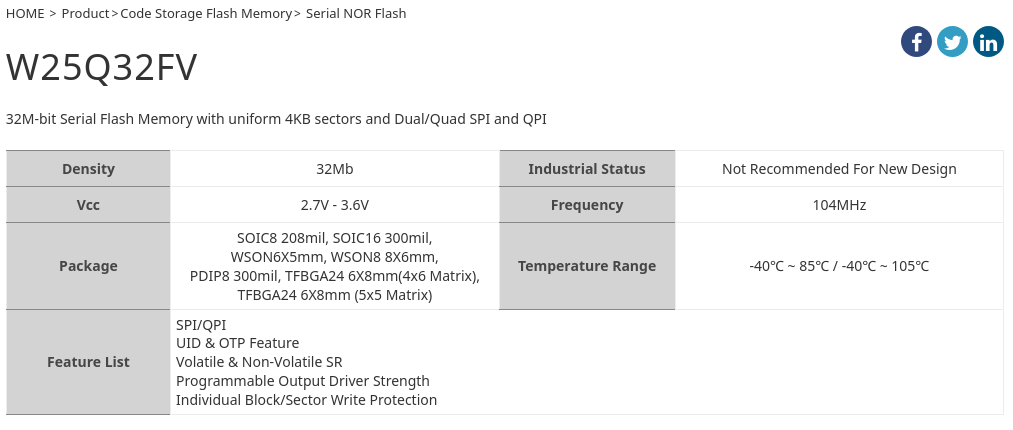
Our chip is the W25Q32FV, so by specifying the chipname
sudo flashrom -V -r blob.bin -p ch341a_spi -c W25Q32FV
I got it to work!
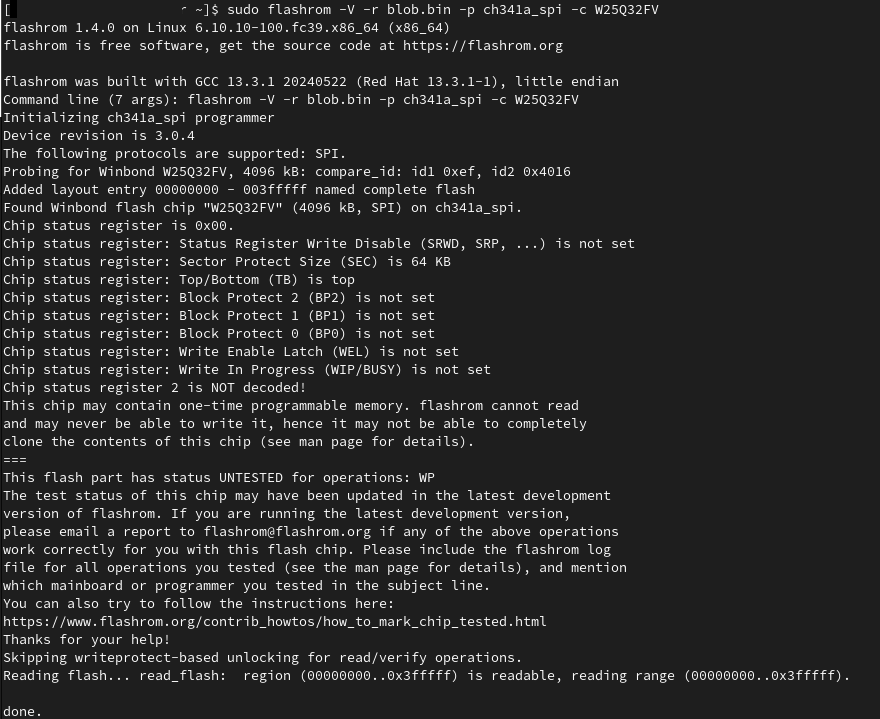
After that, we can start to analyze our blob.bin
Firmware Analysis
We now have our blob.bin. First of all, let's do a "binwalk"
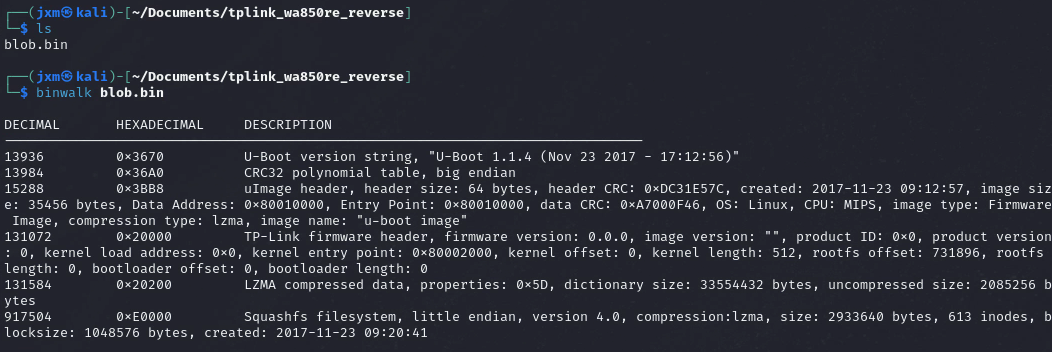
That's something! The thing I'm interested the most is the last section, the squashFS Filesystem.
Basically, SquashFS is a read-only and LZMA-compressed file system for linux, that is usually used in the Live-CD version of the most common distros and on embedded distribution (such as OpenWRT). If we get to that one, we could potentially access to the entire file system of the repeater, including the source code.
If we try to extract the filesystem and access it we get an error, though
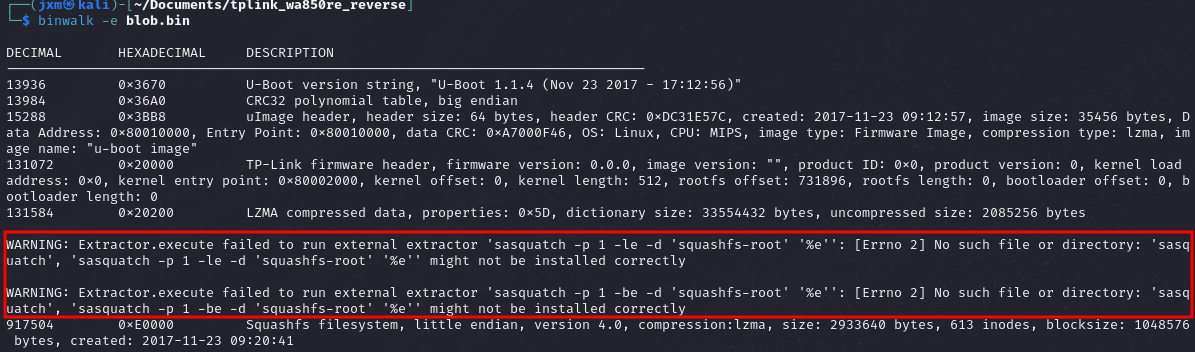
The package "sasquatch" seems to be missing. But what's that? As far as I understand, vendors like to mess up the standard implementation of SquashFS (because why not), and the Sasquatch projects tries to overcome this problem by applying a set of patches to the standard unsquashfs utility.
We can compile it ourselves, but if you are on Kali,
sudo apt install sasquatch
should be enough.
After this step, we should be able to get to the actual content of the SquashFS filesystem.
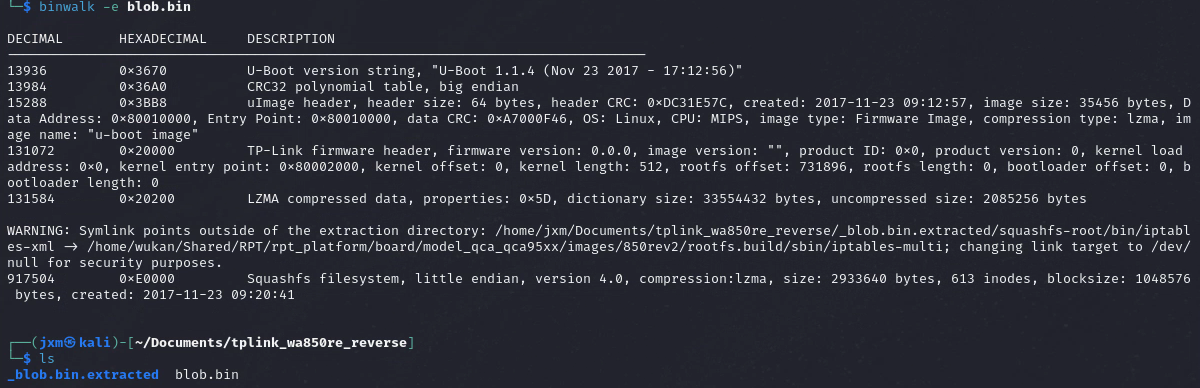
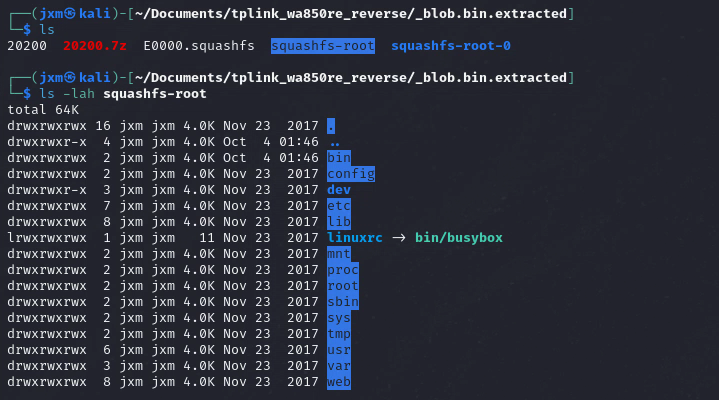
Yes! we did it!
/web
The /web folder of the extracted file system seems to contain the source code of the management web service of the Wi-Fi extender
The /web/data folder seems to be quite interesting, because it contains a lot of JSON files describing various aspect of the repeater.
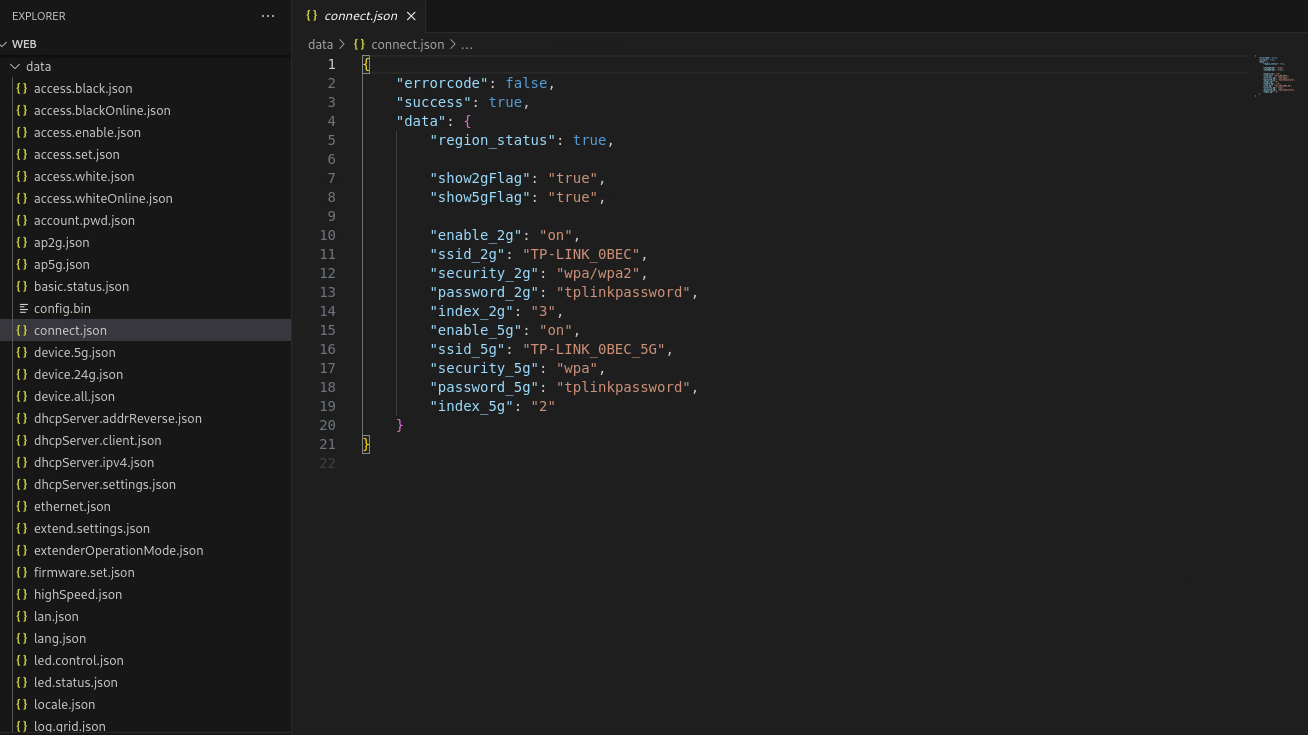
They seem to be mock data though, because if I power up the extender (that to my surprise seems to work quite good) the network is called differently and has a different password. That doesn't surprise me, because the file system contained on the chip is read only, so information like current WiFi name and password are probably stored elsewhere.
Conclusion
My knowledge of the embedded Linux world and the firmware reverse engineering, or whatever this thing that I've tried to do today is called, is really limited, but this small journey has been quite fun.
There's a lot that I left unpacked today: the "U-Boot" and "TP-Link Firmware" sections of blob.bin, other files on the file system, and how the web service really works. There are so many super interesting topics I would love to do deep dives on!
I hope to have enough perseverance to make other posts about this :)
0x00
